Table of Contents
Related Blogs
Popular mobile games are under constant attack from threat actors trying to cheat in multiplayer games, bypass DLC purchases, bypass microtransactions, and those just trying to prove they could hack a game. Cheating reduces player trust and leads to fewer users, which reduces revenue and investment into a game.
Unity Among Mobile Game Apps
To understand how programming choices impact security, we analyzed 58 of the top Android gaming applications. While mobile games are built with a diverse range of languages and frameworks, our research confirms Unity’s overwhelming footprint in the current development landscape:
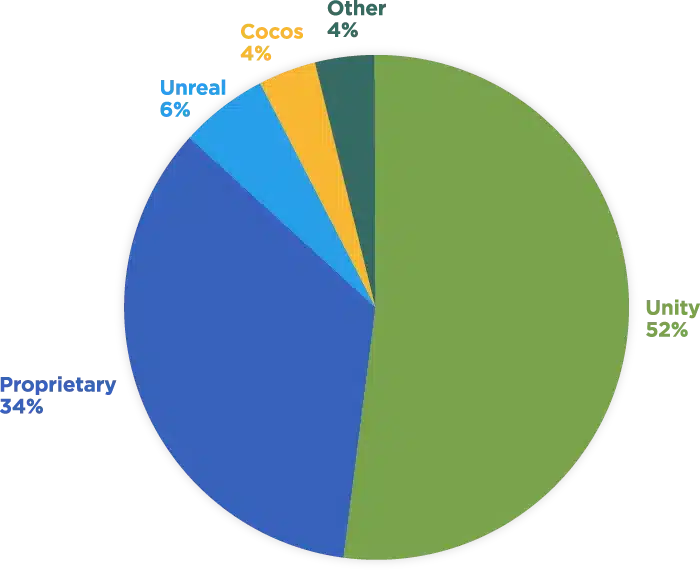
- 27 games used Unity
- 18 games used proprietary frameworks
- 3 games used Unreal
- 2 games used Cocos
- 8 games used some other framework
The data is clear. Protecting games requires protecting Unity applications, while also being flexible enough to support a wide variety of different engines, programming languages, and framework designs. Unity applications have game logic that is written in C# and is compiled into native assembly. Unity also adds common runtime components and dependencies into an application binary, which can be consistent areas for threat actors to focus and transfer their knowledge between games.
Motivations Behind the Cheating
Game cheaters have many different motivations.
In a banking application, the threat actors might do an analysis, weighing how much money they can make committing fraud against how much effort it costs to reverse engineer and modify the app. Whereas, in video games the threat actors might try to make money, but they often don’t value their time this way and might be more motivated by proving they can cheat, breaking the game, damaging the reputation of the company that produced the game, or simply making sure they can’t lose.
Securing a game requires thorough solutions and regular updates against new attacks.
Powering Up, Skipping the Grind
Cheating in mobile games can take many forms based on the game design and the goal of the cheater. Let’s take a look at common cheats before we look at the solutions.
- Client-side memory editing
- Scanning memory using tools like GameGuardian and finding critical variables. Player health, ammo, currency, player location, player speed, or any game specific values. Then modifying those values to benefit the player.
- Modern multiplayer game designs move many of these elements to the server to reduce cheating, but cheaters can be creative and find related values to modify or communication messages to manipulate.
- Repackaging the mobile game with new logic
- Adding new code to the game to benefit the players. This could be modifications to view hidden maps, highlighting choices that should be unknown to the player, or gaining information about competing players that exist in memory but are not drawn on the user interface.
- Botting
- Bots can be added into the game binary to automate player choices and gain advantages. Bots can take many forms. It can be modifications to the binary itself, an emulator that can automate button clicks, or a script that sends messages to mimic gameplay even if the game is not being played as intended.
- Exploiting game logic
- This requires reverse engineering of the game logic itself and finding unintended paths that give a player advantages using knowledge that does not exist in the game interface or online resources.
- Bypassing Purchases
- Stealing in-game currencies, art assets, and downloadable content that are available for purchase uses many of the same techniques as other forms of cheating on this list. In many cases this content already exists in the game files and the software performs a validation check access. Validation checks can be removed by reverse engineering and editing the game software, allowing the user to take actions that would require currency or content where the account should not have access.
- In cases where content is downloaded from the server to provide access, it can be more difficult to bypass the purchase, but cheaters will distribute this content for other users to access without paying. All these attacks require modifying game files, memory, or network messages.
- Account Sharing
- Accounts can be shared to give someone progress in a game without playing it themselves. Account sharing can be a paid service and put the users at risk of losing their information or game progress. These issues can be outside of the binary itself and require monitoring services to track user and threat behavior to shut them down.
Protect the Game
This month, Digital.ai is releasing a brand-new way to protect native Android mobile games, with specific support for handling metadata unique to Unity games. This is in addition to the existing iOS solution.
Our application hardening solution can automatically protect fully built apps with a simple drag-and-drop, command line, or CI integrated interface. This solution will
- Automatically provide protection against static analysis through obfuscation and targeted encryption that leads to memory editing and exploiting game logic.
- Check the game code, data, and asset files to protect against repackaging and game modifications.
- Detect dynamic tools like GameGuardian, Frida, debuggers, roots/jailbreaks, and emulators which help cheaters reverse engineer and modify the game.
- Monitor threats to inform the next revision of protections and track accounts with malicious behavior. Malicious behavior can be responded to immediately for a quick response or periodically ban malicious accounts to make it difficult to track how they were caught.
- Protect against botting and modification techniques (through our White-box Cryptography solution) that rely on reading or modifying client-server communication by encrypting communication and preventing cheaters from finding an encryption key to bypass the security.
When all these protections are combined, it becomes incredibly difficult—one might even say impossible, or at least too hard to bother—to cheat. The user experience and business revenue is secured to keep the game profitable with a growing user base running for a long time.
* Digital.ai and its products and services are not sponsored by or affiliated with Unity Technologies or its affiliates. Unity is a trademark or registered trademark of Unity Technologies or its affiliates in the U.S. and elsewhere.

Protect your in-game revenue and player trust with enterprise-grade mobile game security.
Explore
What's New In The World of Digital.ai
From Defense Labs to Mobile Apps: How Application Protection Grew Up
2001 was a turning point for application security, though few…
The Shrek School of Application Security
Or, How I Learned to Stop Worrying and Love the…
When AI Accelerates Everything, Security Has to Get Smarter
Software delivery has entered a new phase. Since 2022, AI-driven…