Table of Contents
Related Blogs
Overview of Reverse Engineering Attacks
Reverse engineering attacks involve deconstructing a software application to understand its underlying code, architecture, and functionality. These attacks are typically carried out by threat actors seeking to uncover sensitive information, such as proprietary algorithms, encryption keys, or paths to back-end servers. By dissecting the code, attackers can gain insights into how an application operates, potentially enabling them to bypass security measures, create counterfeit versions, or exploit applications for malicious purposes. This form of attack poses significant risks to software developers and enterprises, particularly those whose applications contain valuable intellectual property or communicate sensitive data such as personally identifiable information (PII).
Types of Reverse Engineering Attacks
Binary Analysis
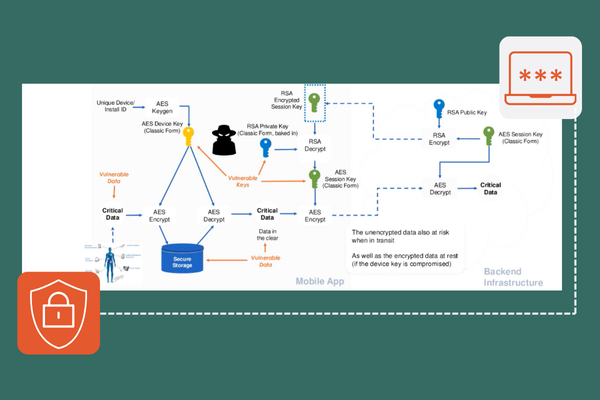
Binary analysis is a form of reverse engineering that involves examining the compiled executable code of an application. Since binaries are machine-readable but not human-readable, attackers use disassemblers and decompilers to convert the binary code back into a more understandable form, often assembly language. This process allows them to identify critical sections of code, such as authentication routines or encryption algorithms, which can then be targeted for exploitation. Binary analysis is particularly dangerous because it can be performed without access to the source code, making it a favored technique for attackers aiming to uncover and exploit secrets and code in applications.
Source Code Analysis
Source code recovery and analysis is the process of retrieving an application’s original source code, or a close approximation of it, from its compiled binary. This can be achieved using advanced decompilation tools that attempt to reverse the compilation process, converting the binary into a high-level programming language. Although the recovered source code may not match the original, it can still provide attackers with a detailed understanding of how the application functions. With access to the source code, attackers can more easily identify vulnerabilities, modify the application for malicious purposes, or create unauthorized copies.
Protocol Reverse Analysis
Protocol reverse engineering involves analyzing the communication protocols used by an application to interact with other systems or devices. Attackers intercept and examine data packets exchanged between the application and its counterparts to understand the communication protocol’s structure, flow, and behavior. By reverse engineering these protocols, attackers can replicate or manipulate the communication, potentially allowing them to impersonate legitimate devices, inject malicious data, or gain unauthorized access to sensitive information. This type of reverse engineering is particularly concerning for applications that rely on proprietary or undocumented protocols for secure communication.
Common Techniques in Reverse Engineering Attacks
Static Analysis
Static analysis is a reverse engineering technique that involves examining the code of an application without actually executing it. This method analyzes the application’s binaries or source code to uncover its structure, logic, and potential vulnerabilities. Tools like disassemblers and decompilers are commonly used in static analysis to convert machine code into a human-readable format, such as assembly language or a higher-level programming language. By carefully studying the code, attackers can identify hardcoded secrets, control flow paths, and potential entry points for exploitation. Static analysis is particularly valuable because it allows attackers to meticulously examine the code in a controlled environment, free from the complexities introduced by runtime behaviors.
Dynamic Analysis
Dynamic analysis, in contrast to static analysis, involves observing an application’s behavior while running. This technique allows attackers to interact with the application in real-time, providing insights into how it processes inputs, handles data, and responds to different conditions. Dynamic Analysis also allows you to modify the binary or its behavior (hooking, swizzling, even changing the assembly itself). Using tools such as debuggers, profilers, and dynamic instrumentation frameworks, attackers can monitor memory usage, trace execution paths, and detect vulnerabilities that may not be apparent through static analysis alone. Dynamic analysis is especially useful for identifying runtime-specific issues, such as memory leaks, race conditions, or unprotected sensitive data in memory, making it a powerful tool in the reverse engineer’s arsenal.
Hybrid Analysis
Hybrid analysis combines the strengths of both static and dynamic analysis to provide a more comprehensive understanding of an application. In the “real world,” every attack is a “Hybrid” attack because real attacks leverage static and dynamic techniques. For example, attackers can map out the application’s overall structure by leveraging static analysis and identifying key areas of interest. Then, through dynamic analysis, they can test and refine their findings by observing how the application behaves under different conditions. This dual approach allows attackers to uncover complex vulnerabilities that may be difficult to detect using either technique alone. Hybrid analysis is particularly effective for reverse engineering sophisticated applications that use obfuscation, anti-tamper measures, or other techniques designed to thwart analysis. By integrating both static and dynamic insights, attackers can achieve a deeper level of understanding, making hybrid analysis a potent tool for dissecting even the most well-protected software.
Tools Used in Reverse Engineering
Disassemblers
Disassemblers are crucial tools in the reverse engineering process, designed to convert machine-level binary code back into assembly language, which is more readable to humans. By translating the raw binary instructions into their corresponding assembly commands, disassemblers provide a detailed view of an application’s low-level operations, including control flow, function calls, and memory accesses. This allows reverse engineers to analyze the underlying logic of the code, identify critical sections, and uncover potential vulnerabilities or hidden functionality. Disassemblers are particularly valuable because they work directly with the compiled binaries, making them effective for analyzing software even when the source code is unavailable. However, interpreting disassembled code can be challenging, as it often requires deep knowledge of assembly language and the architecture on which the application runs. A couple of examples of disassembler tools are IDAPro and Ghidra.
Debuggers
Debuggers are essential tools in reverse engineering, used to analyze and manipulate the execution of an application in real time. Debuggers provide deep insights into the application’s behavior by allowing reverse engineers to pause, step through, and inspect the state of a program as it runs. This includes examining the contents of memory, registers, and variables at specific points in the execution flow, which can reveal hidden functionality or vulnerabilities that aren’t immediately apparent from static analysis alone. Debuggers are particularly useful for identifying runtime issues, such as buffer overflows or improper handling of user inputs. They also allow reverse engineers to modify code on the fly, test hypotheses, and observe the effects of changes in a controlled environment. Common debuggers like GDB, WinDbg, and LLDB are integral to the reverse engineering process, helping analysts dissect and understand complex software systems. Proprietary and automated testing products and solutions include sophisticated debuggers.
Decompilers
Decompilers are tools used in reverse engineering to convert compiled binary code back into a higher-level programming language, such as C, C++, or Java. This process helps reverse engineers understand the original source code logic and structure. Decompilers are especially valuable for analyzing complex software and understanding how a particular application functions. However, the output from decompilers is often imperfect, as some information is lost during the compilation process, making the recovered code less readable than the original. Popular decompilers include open-source tools commonly used for decompiling Java bytecode, like JD-GUI and CFR. Hex-Rays Decompiler is a well-known proprietary tool, often used with IDA Pro, providing powerful decompilation capabilities for various architectures. Another notable decompiler is Ghidra, which is open-source and supports multiple programming languages and architectures, making it a versatile tool in the reverse engineering community. These tools are integral for understanding and analyzing application software at a deep level.
Network Analyzers
Network analyzers, or packet sniffers or protocol analyzers, are tools used to capture, inspect, and analyze network traffic in real time. These tools are essential for reverse engineers and security professionals who must understand the communication patterns and protocols used by applications or systems over a network. Network analyzers allow users to monitor data packets as they travel across a network, providing insights into the traffic’s content, source, destination, and timing. This information is invaluable for identifying potential security issues, debugging network problems, or reverse engineering proprietary communication protocols.
The most popular network analyzer is Wireshark. Wireshark is known for its powerful features and extensive protocol support, allowing users to capture and interactively browse traffic on a network, making it a go-to tool for network troubleshooting and reverse engineering.
Hex Editors
Hex editors are specialized tools used to view and modify the raw binary data of files, allowing users to interact directly with the hexadecimal representation of the file’s contents. This low-level access is crucial in reverse engineering, where understanding and altering the precise byte-level structure of an executable, data file, or memory dump can reveal hidden information, modify behavior, or bypass certain security measures. Hex editors display data in hexadecimal format alongside the corresponding ASCII representation, making identifying patterns, strings, or specific data structures easier. They are commonly used for tasks such as patching software, analyzing malware, or inspecting file headers.
A couple of examples of popular hex editors are:
- HxD is a free, fast, and user-friendly hex editor for Windows that offers a wide range of features, including file comparison, data analysis, and the ability to work with large files. It’s widely used for both simple edits and complex reverse engineering tasks.
- Hex Fiend is a free, open-source hex editor designed for macOS. It’s known for its quick handling of large files and intuitive interface, making it a popular choice among macOS users.
Motivations Behind Reverse Engineering Attacks
Intellectual Property Theft
One of the primary motivations for threat actors to engage in reverse engineering attacks is the theft of intellectual property (IP). Software companies invest significant time, resources, and expertise in developing proprietary algorithms, encryption techniques, and other innovative technologies that give them a competitive edge. By reverse engineering these applications, attackers can uncover and steal these valuable assets, which can then be replicated, sold, or integrated into competing products. This type of theft results in direct financial losses, undermines the victim’s market position, and erodes trust with customers. For industries where IP is the cornerstone of business success, reverse engineering attacks pose a serious threat that can have long-lasting implications.
Software Cracking
Software cracking is another common motivation behind reverse engineering attacks, particularly in the financial services, gaming, and media industries. Financial services are an obvious target for threat actors because they have the money. Games are a target for a group of highly technical and highly motivated threat actors. Media companies create applications that incorporate robust security measures, such as digital rights management (DRM) or license validation, to protect their software from unauthorized use and piracy. However, by reverse engineering the application, threat actors can bypass these protections, enabling them to distribute cracked versions of the software that can be used without paying for licenses or subscriptions. In the financial services industry, cracked applications can be used to engage in fraudulent activities, while in gaming and media, they facilitate piracy, leading to significant revenue losses. Software cracking undermines the business models of these industries and poses security risks to users who may unknowingly download compromised or malicious versions of the software.
Competitive Intelligence
Threat actors also employ reverse engineering to gain a competitive advantage through competitive intelligence. By dissecting a rival’s software, companies can glean insights into their competitors’ technical capabilities, design choices, and strategic directions. This information can be used to improve their products, anticipate market trends, or identify weaknesses in a competitor’s offerings. While competitive intelligence through reverse engineering may sometimes operate in a legal gray area, it often crosses into unethical or illegal territory, particularly when it involves the unauthorized use of proprietary information. This practice can destabilize industries where innovation and technological advancement are key drivers of success.
Case Studies and Examples
Notable Reverse Engineering Attacks
Apple iOS Jailbreaking
Apple’s iOS operating system has been the target of numerous reverse engineering attacks, leading to the widespread practice of jailbreaking. Reverse engineers exploit vulnerabilities in iOS to gain root access, allowing users to bypass Apple’s restrictions and install unauthorized apps, customize the user interface, and more. While some users jailbreak their devices for legitimate customization, the practice has also led to security risks and the proliferation of pirated apps. Over the years, Apple has continuously updated iOS to patch vulnerabilities and prevent jailbreaking. Still, reverse engineers persist in finding new methods, creating an ongoing cat-and-mouse game between Apple and the jailbreaking community.
Magecart
Magecart is a collective name for a group of cybercriminal organizations that have been active since around 2015, specializing in web skimming attacks. These attacks typically target e-commerce websites, aiming to steal credit card information and other sensitive data directly from users during the checkout process. Magecart attacks often involve the reverse engineering of website code to identify vulnerable entry points where malicious scripts can be injected.
Once the attackers gain access to the site, usually by exploiting known vulnerabilities in third-party plugins or compromising the supply chain, they insert JavaScript code that silently captures payment details as customers enter them. The stolen data is then transmitted to servers controlled by the attackers, allowing them to commit fraud or sell the information on the dark web.
One of the most notable Magecart attacks occurred in 2018 when the group successfully compromised the payment systems of major companies like British Airways and Ticketmaster. The British Airways breach, for example, affected over 380,000 transactions, leading to significant financial losses and reputational damage for the company. The incident underscored the risks associated with third-party dependencies in web applications and highlighted the sophisticated techniques used by Magecart groups to reverse engineer and exploit web-based systems.
Magecart’s approach, leveraging reverse engineering to identify and exploit vulnerabilities in web infrastructure, has made it one of the most persistent and damaging threats to e-commerce security in recent years.
Defense Mechanisms Against Reverse Engineering
Defending against reverse engineers requires a multi-layered approach that includes several key strategies. Code obfuscation is the first line of defense, making the source code difficult to understand by transforming it into a form that is still functional but unreadable to human analysts. This technique deters reverse engineers by increasing the complexity and effort required to analyze the code. Anti-tamper mechanisms add another layer of protection by detecting and responding to unauthorized code modifications, such as attempts to alter or bypass security features, often by shutting down the application or triggering alerts. Threat monitoring involves continuously observing the application’s environment to detect suspicious activities indicating an ongoing reverse engineering attempt, such as unusual debugging behaviors or code modifications, allowing for real-time responses to potential threats. Finally, Runtime Application Self-Protection (RASP) integrates security directly into the application, enabling it to monitor and protect itself against attacks while running. RASP can detect and block attempts to exploit vulnerabilities, making it significantly harder for reverse engineers to manipulate the application during execution. Together, these strategies create a robust defense against reverse engineering attacks, helping to safeguard sensitive intellectual property and maintain the integrity of the application.
Legal and Ethical Considerations
Reverse engineering sits at a complex intersection of legal and ethical considerations. Legally, reverse engineering can be both permissible and prohibited, depending on the context, jurisdiction, and specific terms of service or licensing agreements. For instance, reverse engineering is allowed in some regions for purposes like interoperability, security research, or educational use, provided it does not violate intellectual property laws or contractual obligations. However, unauthorized reverse engineering to steal proprietary technologies, bypass security mechanisms, or create counterfeit products is illegal and can result in severe penalties, including lawsuits and criminal charges. Ethically, reverse engineering is a gray area; while it can contribute to innovation, security improvements, and academic knowledge, it can also be misused for malicious purposes, such as software piracy, espionage, or compromising the privacy and security of users. The ethical implications often depend on the intent and impact of the reverse engineering activities, making it crucial for practitioners to consider both legal constraints and the broader consequences of their actions.
Summary of Key Points
In conclusion, reverse engineering attacks represent a significant threat to the security and integrity of software applications, with motivations ranging from intellectual property theft to competitive intelligence. Organizations can better prepare and implement robust defenses such as code obfuscation, anti-tamper mechanisms, threat monitoring, and Runtime Application Self-Protection (RASP) by understanding the types of reverse engineering techniques and notable past attacks. While reverse engineering has legal and ethical complexities, a comprehensive security strategy can help safeguard valuable assets and maintain trust in today’s app-happy world.
Protect Applications Against Reverse Engineering
Explore
What's New In The World of Digital.ai
Announcing Quick Protect Agent: MASVS-Aligned Protections, Now Easier Than Ever
Easily apply OWASP MASVS-aligned protections to your mobile apps—no coding needed. Quick Protect Agent delivers enterprise-grade security in minutes.
“Think Like a Hacker” Webinar Recap: How AI is Reshaping App Security
Discover how generative AI is reshaping app security—empowering both developers and hackers. Learn key strategies to defend against AI-powered threats.
The Encryption Mandate: A Deep Dive into Securing Data in 2025
Discover how white-box cryptography and advanced encryption help enterprises secure sensitive data, meet compliance, and stay ahead of cybersecurity threats.