Mobile App Hardening
Mobile app hardening protects your iOS and Android apps from tampering, reverse engineering, and runtime attacks.
Digital.ai combines automated hardening with Runtime Application Self‑Protection (RASP) to defend sensitive data, application logic, and user trust—even in high‑risk environments.
- Automatically apply multilayer mobile app protection without changing source code.
- Detect and prevent runtime threats with built‑in RASP capabilities.
- Integrate security directly into CI/CD pipelines for scalable enterprise protection.
Request a Demo
Trusted By Enterprise Customers
Why Is Mobile App Hardening Important?
Today’s mobile applications operate in high-risk environments where attackers routinely analyze, modify, or exploit apps to gain access to sensitive data. Even well-built apps can be compromised without protection, exposing organizations to fraud, compliance issues, and brand damage.
Mobile app hardening gives development, security, and product teams the confidence that their apps can withstand real-world attacks. By proactively defending mobile apps, organizations reduce risk, improve user trust, and maintain compliance with industry security requirements.

How Digital.ai Approaches Mobile App Hardening
Digital.ai delivers enterprise-grade mobile app hardening with automated security, strong obfuscation, and runtime protection built directly into the binary. Teams can protect mobile apps without changing code, adding SDKs, or increasing development complexity.
The solution delivers scalable, layered protection for all your mobile applications, defending against sophisticated threats without requiring code changes or additional engineering effort. Digital.ai helps organizations stay ahead of evolving threats by combining static protection with dynamic runtime safeguards.
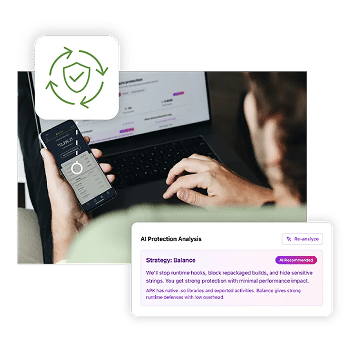
Mobile App Hardening Capabilities
Advanced Code Obfuscation
Conceals sensitive logic with layered transformations that make analysis and reconstruction significantly harder for attackers.
Runtime Application Self-Protection (RASP)
Monitors app behavior and blocks tampering, hooking, and dynamic analysis during execution.
Anti‑Reverse Engineering Controls
Disrupts static and dynamic inspection to prevent understanding or replicating app functionality.
Root and Jailbreak Detection
Identifies compromised devices and enforces security policies to reduce exposure.
Anti‑Tampering and Anti‑Debugging
Detects unauthorized modification or debugging and stops execution when threats appear.
Secure Data and Key Protection
Protects sensitive information and cryptographic keys from exposure or extraction.
Attacks Are Rising On Client Apps—Are Your Defenses Keeping Up?














