Table of Contents
Table of Contents
Related Blogs
Common Threats to Client-Side Security
Client-side applications, such as web, mobile, and desktop apps, are highly accessible to users, including malicious actors. This accessibility makes them vulnerable to a range of attacks. Reverse engineering allows attackers to dissect and understand the code, which can lead to exploits or the discovery of sensitive information. For instance, the code might include instructions on how to access back-office systems. Another prevalent threat is cross-site scripting (XSS), where attackers inject malicious scripts into web applications, compromising user data or control of the app. Cross-site request forgery (CSRF) attacks trick users into executing unwanted actions within an app. Additionally, malicious script injections and browser-based attacks like formjacking or Magecart can exploit vulnerabilities in client-side code, leading to severe data breaches and unauthorized access. Protecting client-side apps requires addressing these threats through robust security practices.
Examples of Client-Side Security Measures
Input Validation and Sanitization
Input validation and sanitization are fundamental techniques for securing client-side applications against malicious data entry. Input validation involves checking the data users provide to ensure it meets expected formats and constraints before processing it. This helps prevent attackers from injecting harmful data, such as SQL queries or malicious scripts, into the application. Sanitization goes further by cleaning or modifying the input to remove or neutralize harmful elements, especially for scenarios like form submissions, URL parameters, or file uploads. Together, these practices help mitigate threats like cross-site scripting (XSS), SQL injection, and other forms of input-based attacks, ensuring that the data flowing into your app is safe and properly handled. Effective validation and sanitization are critical first lines of defense for any client-side security strategy.
Content Security Policy (CSP)
Content Security Policy (CSP) is a powerful security feature designed to prevent various attacks, such as cross-site scripting (XSS) and data injection. CSP works by allowing developers to define a whitelist of trusted content sources that the browser is permitted to load and execute, such as scripts, images, and styles. By restricting content to these approved sources, CSP blocks any unauthorized or malicious scripts from running, even if they have been injected into the application. While this proactive approach significantly reduces the attack surface by making it harder for threat actors to execute harmful actions through browser-based vulnerabilities, it is not considered 100% foolproof, prompting a search for complementary security measures. Implementing CSP is essential in fortifying client-side security and ensuring that only trusted, vetted resources interact with web applications.
White-box Cryptography
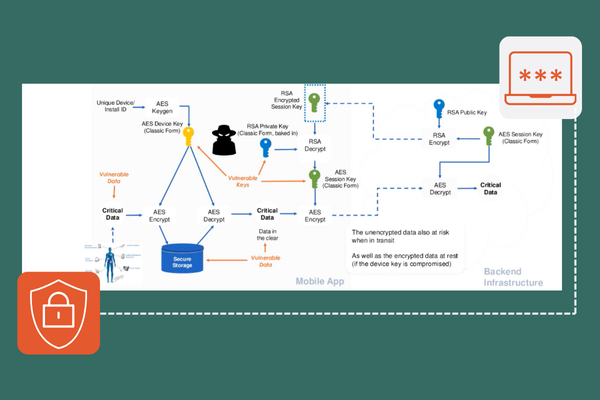
White-box cryptography is a specialized approach to securing cryptographic operations, particularly in environments where the code and execution are fully exposed to attackers, such as client-side applications. Traditional cryptography assumes the execution environment is secure, but white-box cryptography is designed to protect cryptographic keys and operations even when an attacker has full access to the software, including the code, memory, and execution flow. In white-box cryptography, the cryptographic algorithm is transformed into a version that conceals the keys within the software, making it extremely difficult for attackers to extract or manipulate them. This technique ensures that sensitive cryptographic operations, like encryption and decryption, remain secure even in compromised or untrusted environments. White-box cryptography is particularly useful in client-side apps where reverse engineering and memory attacks are common threats.
Runtime Application Self-Protection
Runtime Application Self-Protection (RASP) is an advanced security measure that allows applications to detect and respond to threats in real-time during execution. Unlike traditional security methods focusing on external protection, RASP is embedded within the application, enabling it to monitor its behavior and environment. When it detects suspicious activity—such as attempts to exploit vulnerabilities, manipulate code, or execute unauthorized commands—RASP can automatically block the actions, terminate the session, or alert security teams. This proactive approach significantly reduces the risk of attacks, such as code injection and unauthorized access, by stopping threats before they compromise the system. RASP is particularly valuable for protecting client-side applications, as it strengthens security even when attackers bypass other external defenses.
Client-Side Threat Monitoring
Client-side threat monitoring involves continuously observing and analyzing the behavior of client-side applications to detect potential security threats in real-time. Since client-side apps are directly accessible by users—and thus, threat actors—this monitoring is crucial to identify malicious activity, such as code tampering, reverse engineering attempts, and unauthorized data access. Effective client-side threat monitoring often integrates with tools like Runtime Application Self-Protection (RASP) and can generate alerts when suspicious activities are detected. It may also include monitoring for indicators of attacks, such as abnormal API calls, unusual input patterns, or the presence of debugging tools. By providing visibility into the client-side environment, threat monitoring enables organizations to quickly respond to potential breaches and continuously adapt their security measures to evolving threats.
Secure Handling of Cookies
The secure handling of cookies, such as session tokens or user preferences, is essential for protecting sensitive data stored on the client side. To ensure security, cookies should be flagged as Secure, meaning they are only transmitted over HTTPS, preventing attackers from intercepting them through man-in-the-middle attacks. The HttpOnly flag should also be used in order to prevent client-side scripts from accessing the cookies, mitigating the risk of cross-site scripting (XSS) attacks. Additionally, setting the SameSite attribute helps control when cookies are sent with cross-site requests, reducing the likelihood of cross-site request forgery (CSRF). For cookies that store sensitive data, ensuring they are properly encrypted and have an expiration time to limit their availability is crucial. These measures work together to prevent unauthorized access and manipulation of cookies, ensuring the confidentiality and integrity of client-side data.
HTTPS and Secure Communication
HTTPS (Hypertext Transfer Protocol Secure) is the standard protocol for ensuring secure communication between a client (e.g., a web browser) and a server. By encrypting the data transmitted over the network using SSL/TLS (Secure Sockets Layer/Transport Layer Security), HTTPS protects sensitive information such as login credentials, payment details, and personal data from being intercepted or tampered with by malicious actors. Unlike HTTP, which transmits data in plaintext, HTTPS ensures that it remains unreadable even if data is intercepted. Additionally, HTTPS verifies the server’s authenticity through digital certificates, preventing man-in-the-middle attacks by ensuring that users are connected to the legitimate server. Implementing HTTPS across all client-server communications is critical for maintaining confidentiality, integrity, and trust in client-side applications.
Subresource Integrity (SRI)
Subresource Integrity (SRI) is a security feature that helps ensure the integrity of external resources, such as scripts or stylesheets, loaded into a web application. SRI allows developers to include a cryptographic hash in the application’s HTML markup. This hash represents the expected content of the external resource, and when the resource is loaded, the browser verifies its integrity by comparing the loaded content against the provided hash. If the content has been altered or tampered with—intentionally by a threat actor or unintentionally during transit—the browser will block the resource from executing. This protects the application from attacks like malicious script injection or compromised third-party libraries, which could otherwise be exploited to perform unauthorized actions or steal sensitive data. Subresource Integrity is a valuable safeguard for ensuring that only trusted and untampered external resources are used in your client-side application.
Code Obfuscation and Anti-Tamper
Code obfuscation is a technique used to protect client-side applications by making the source code difficult for attackers to read, understand, or reverse-engineer. Through obfuscation, elements such as function names, variables, and logic are transformed into ambiguous and unreadable formats without altering the code’s functionality. This prevents malicious actors from easily identifying vulnerabilities or extracting sensitive information. Anti-tamper mechanisms add another layer of defense by detecting and responding to unauthorized code modification when paired with obfuscation. If tampering is detected, anti-tamper tools can halt the execution of an application, alert security teams, or trigger self-destruct mechanisms to prevent further exploitation. Together, code obfuscation and anti-tamper techniques play a critical role in protecting intellectual property and maintaining the integrity of client-side applications, making it much harder for attackers to analyze or manipulate the code for malicious purposes.
Implementation Strategies for Client-Side Security
Implementing effective client-side security requires a multi-layered approach that combines a variety of techniques to protect applications from a broad range of threats. Code obfuscation and anti-tamper measures should be used to protect the integrity of the code and prevent reverse engineering. Input validation and sanitization safeguard against injection attacks by properly handling all user input before processing. Content Security Policies (CSP) help limit the execution of unauthorized scripts, while Subresource Integrity (SRI) verifies the authenticity of third-party resources. Ensuring secure cookie handling and enforcing HTTPS for secure communication are fundamental practices for maintaining confidentiality and data integrity. Additionally, integrating Runtime Application Self-Protection (RASP) allows applications to monitor themselves and react to suspicious activity in real-time. A comprehensive client-side security strategy combines these tools and practices, addressing both prevention and real-time threat detection to minimize vulnerabilities and ensure robust protection.
Secure JavaScript Coding Practices
Ensuring secure JavaScript coding practices protects client-side applications from common security threats. One key practice is avoiding the use of `eval()` and similar functions that allow dynamic code execution, as they can be exploited for script injection attacks like XSS. Developers should also ensure that input validation and sanitization are rigorously applied, preventing malicious input from compromising the application. Limiting the exposure of sensitive data within the code and using environment variables for sensitive configurations can reduce the risk of unauthorized access. Additionally, employing strict mode (`use strict`) helps enforce a cleaner, safer codebase by catching common coding errors and reducing unsafe actions. Secure communication channels, such as HTTPS, ensure that JavaScript does not transmit sensitive data over unsecured connections. Finally, implementing code obfuscation further protects JavaScript from reverse engineering by making the source code difficult to understand, while Subresource Integrity (SRI) ensures that external scripts are not tampered with. Together, these practices help to create a more resilient and secure JavaScript environment.
Using Security Libraries and Frameworks
Security libraries and frameworks provide developers with ready-to-use solutions for implementing best practices and protecting client-side applications. These tools reduce the likelihood of introducing vulnerabilities by offering well-tested methods for handling tasks like input validation, data encryption, and secure authentication. For example, Helmet.js is commonly used in Node.js applications to set HTTP headers that protect against a variety of attacks, including cross-site scripting (XSS) and cross-site request forgery (CSRF). CSURF is another library that helps safeguard applications from CSRF attacks. Frameworks like React and Angular also embed security features like automatic content sanitization and mechanisms to prevent template injection. These libraries and frameworks are continually updated to address new vulnerabilities and attack vectors, enabling developers to stay current with evolving security standards. By incorporating security-focused libraries and frameworks into development workflows, teams can create more secure applications while reducing the need to implement complex security features manually.
Case Studies of Client-Side Security Breaches
Understanding real-world cases of client-side security breaches can provide valuable insights into the consequences of insufficient protection and the tactics employed by attackers. These incidents highlight the importance of implementing strong client-side security measures, from major data breaches to exploits of common vulnerabilities like cross-site scripting (XSS) and cross-site request forgery (CSRF). The following case studies focus on well-known breaches and the lessons they offer for securing client-side applications.
Real-World Examples of XSS Attacks
One of the most notorious XSS attacks occurred in 2014 when the popular social media platform eBay was exploited by attackers using cross-site scripting. Malicious code was injected into eBay’s listings, allowing attackers to steal login credentials and personal information when users clicked on infected links. The vulnerability arose because eBay failed to properly sanitize user input, enabling attackers to insert malicious JavaScript into the HTML code of the listings. Another significant example is the British Airways breach in 2018, where attackers used XSS to inject a malicious script that stole customer payment data from the airline’s website. In both cases, inadequate input validation and lack of strong content security measures led to large-scale data theft, highlighting the critical need for robust XSS defenses like input sanitization and content security policies (CSP).
Instances of Successful Clickjacking
Clickjacking is a technique in which attackers trick users into unknowingly clicking on something different from what they perceive, often leading to serious security breaches. One infamous example is the 2010 Twitter clickjacking attack, where a malicious link unknowingly caused users to retweet a specific tweet without their consent. Users who visited an infected website would click on what appeared to be a harmless button, but in reality, they were activating a hidden Twitter feature. Another example occurred in 2014 when Facebook was targeted through a clickjacking attack that caused users to “like” pages or share links without realizing it. Attackers used invisible frames (iframes) placed over legitimate buttons to hijack user clicks, exploiting social networks’ trust and rapidly spreading malicious content. These instances underscore the importance of implementing X-Frame-Options headers or Content Security Policy (CSP) to prevent such attacks by controlling how web pages are embedded in iframes.
High-Profile CSRF Vulnerabilities
Cross-Site Request Forgery (CSRF) vulnerabilities have been exploited in several high-profile incidents, exposing weaknesses in how web applications handle user sessions and requests. One notable case occurred in 2008 when YouTube was targeted by a CSRF attack that allowed hackers to alter comments on videos, attributing comments to unsuspecting users. Another well-known instance took place in 2010 when Django, a popular web framework, was found to be vulnerable to CSRF, which could have allowed attackers to hijack user accounts or perform unauthorized actions like changing user settings. In both cases, CSRF tokens—unique, unpredictable values tied to each session—were implemented as part of the solution to prevent unauthorized actions. Despite these fixes, CSRF vulnerabilities remain a risk in many web applications that do not properly validate user requests or segregate sensitive actions from standard sessions. These incidents underscore the importance of integrating robust anti-CSRF measures in any application dealing with sensitive user data or functionality.
Documented Man-in-the-Browser Attacks
Here are some examples of documented Man-in-the-Browser (MitB) attacks:
- Zeus Trojan: One of the most notorious Man-in-the-Browser attacks, the Zeus Trojan (also known as Zbot), targeted banking credentials. It would infect users’ browsers, usually through phishing emails, and inject itself into online banking sessions. Once users logged into their banking accounts, Zeus would intercept login credentials and manipulate transactions, redirecting funds to accounts controlled by attackers. Zeus infected millions of computers globally and was responsible for significant financial losses.
- SpyEye Trojan: A close relative of the Zeus Trojan, SpyEye also targeted online banking users. It used web injections to alter how banking websites appeared to victims, tricking them into providing additional information or redirecting funds. SpyEye was particularly dangerous because it could work with other malware like Zeus, making the attack even more powerful.
- Gozi Trojan: This sophisticated malware was another example of a MitB attack. The Gozi Trojan infected users’ browsers and monitored their online activities, particularly targeting financial institutions. Gozi would remain dormant until it detected an online banking session, at which point it would activate and steal login credentials or alter transactions in real time.
- Tinba (Tiny Banker) Trojan: This lightweight banking Trojan infected users’ browsers and injected malicious scripts into legitimate banking websites. Tinba could alter transaction details without the user’s knowledge, often leading to the theft of funds. It was particularly effective because of its small size and ability to remain undetected for long periods.
These attacks highlight the effectiveness of Man-in-the-Browser attacks in financial fraud, with banking and e-commerce platforms being prime targets. To protect against such attacks, multi-factor authentication, regular software updates, and strong security software are crucial.
Tools and Resources for Enhancing Client-Side Security
Popular JavaScript Security Libraries
JavaScript security libraries are essential tools for developers looking to safeguard client-side applications against various vulnerabilities. Some popular options include:
- DOMPurify: A library that sanitizes HTML and prevents cross-site scripting (XSS) attacks by removing malicious scripts from user inputs.
- jsSHA: A cryptographic library designed for secure hashing and authentication to safeguard sensitive data in JavaScript applications.
- CSRF: A Node.js library that provides CSRF protection by generating tokens to secure user sessions.
- Helmet.js: A Node.js security middleware that sets various HTTP headers to enhance application security and reduce the risk of common web vulnerabilities.
These libraries are highly regarded for enhancing the security posture of client-side apps by addressing common security challenges efficiently.

Application Security for Mobile
Explore
What's New In The World of Digital.ai
Announcing Quick Protect Agent: MASVS-Aligned Protections, Now Easier Than Ever
Easily apply OWASP MASVS-aligned protections to your mobile apps—no coding needed. Quick Protect Agent delivers enterprise-grade security in minutes.
“Think Like a Hacker” Webinar Recap: How AI is Reshaping App Security
Discover how generative AI is reshaping app security—empowering both developers and hackers. Learn key strategies to defend against AI-powered threats.
The Encryption Mandate: A Deep Dive into Securing Data in 2025
Discover how white-box cryptography and advanced encryption help enterprises secure sensitive data, meet compliance, and stay ahead of cybersecurity threats.