Table of Contents
Related Blogs
In our recent webinar, “Think Like a Hacker: Securing Apps in an AI-Driven Landscape,” Senior Product Marketing Manager Dan Shugrue and Field CTO Adam Kentosh took attendees on a deep dive into the evolving threat landscape shaped by AI. The session was an exploration of how generative AI tools are empowering both developers and hackers, and why enterprises must rethink their approach to application security to stay ahead.
Here’s a quick recap of the webinar, highlighting key themes, insights, and strategies shared during the event.
The Double-Edged Sword of AI
The webinar began with an in-depth look at how AI has revolutionized software development. Tools like large language models (LLMs) have transformed coding workflows, enabling developers to write, refactor, and document code faster than ever before. According to McKinsey, these tools can boost productivity by as much as 45%. GitHub surveys also reveal that developers feel more focused and satisfied when using AI assistants.
But this same technology is being weaponized by hackers. Generative AI has lowered the barrier to entry for cybercriminals, allowing them to create sophisticated malware, automate attack chains, and scale operations at unprecedented speeds. The democratization of hacking tools has ushered in an era where even novice attackers can exploit vulnerabilities with alarming precision.
A World of Vulnerable Apps
Shugrue painted a vivid picture of the modern app ecosystem—one where mobile apps have become ubiquitous across industries like finance, retail, automotive, and healthcare. While apps deliver convenience and innovation to consumers, they also expose enterprises to new and significant risks.
Every application is essentially a blueprint for accessing backend servers or sensitive systems. And with millions of mobile apps now in circulation, the challenge for enterprises has shifted from rapid development to ensuring robust security—a task made even more urgent by the rise of AI-powered attacks.
The Hacker’s Toolkit: LLMs in Action
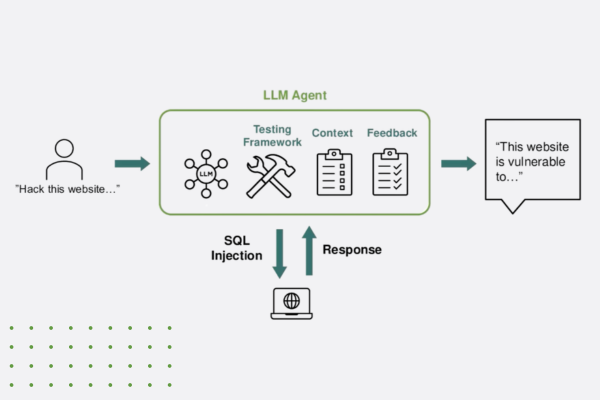
Kentosh brought these concepts to life with a live demonstration of how LLMs can help hackers rapidly exploit mobile apps. Using freely available tools like JADX to decompile an Android APK, he showed how attackers can reverse-engineer code to uncover vulnerabilities like hardcoded credentials or insecure API endpoints.
The most compelling moment of the demonstration came when decompiled code was fed into an LLM and asked it to analyze security weaknesses. Within seconds, the model identified vulnerabilities and even suggested tailored attack strategies. It didn’t stop there—the LLM generated scripts for launching denial-of-service (DDoS) attacks and iteratively refined them based on server responses.
The bottom line? Modern LLMs can now orchestrate entire attack sequences against a website with very minimal input needed from the threat actor using agentic AI. Hackers no longer need deep technical expertise; they simply need access to an LLM and merely a few minutes (or even seconds) of their time.
The Imperative for Proactive Security
Given the scale and sophistication of modern threats, Digital.ai’s experts emphasized that traditional reactive security measures are no longer sufficient. Enterprises must embed security directly into their software development lifecycle (SDLC) and adopt proactive defenses that neutralize threats before they escalate.
Shugrue outlined several strategies for securing apps:
- Code Obfuscation: By making code difficult to reverse-engineer, obfuscation disrupts pattern recognition by LLMs and forces attackers to expend more time and effort.
- Runtime Application Self-Protection (RASP): Applications should be able to detect compromised environments, like emulators or root-jailbroken devices, and respond automatically.
- White-box Cryptography: This advanced technique ensures that cryptographic operations remain secure even when attackers have full access to the client-side environment.
These measures align with industry standards, such as the OWASP Mobile Application Security Verification Standard (MASVS), which provides a framework for building resilient mobile applications.
White-Box Cryptography: A Critical Layer of Defense
The webinar concluded with an exploration of white-box cryptography, which Shugrue described as essential for protecting sensitive keys and operations in hostile environments, such as client-side devices. Unlike traditional cryptography models that assume endpoints are secure, white box cryptography is purpose-built for situations where attackers have full visibility into running software.
By embedding cryptographic keys directly into application binaries—and ensuring they can only be used with matching libraries—white-box cryptography prevents attackers from extracting or misusing sensitive data. This technique is particularly valuable for industries like healthcare and finance, which handle highly sensitive information.
Key Takeaways
The “Think Like a Hacker” webinar was both sobering and empowering. It highlighted how generative AI is reshaping the cybersecurity landscape while offering actionable strategies for enterprises to defend their applications without slowing down innovation.
Here are four key takeaways from the session:
- AI is accelerating both development and attacks: Enterprises must adapt quickly to this new reality by embedding security into their SDLC.
- Proactive measures are essential: Code obfuscation, RASP, and white-box cryptography can neutralize threats before they escalate and deter threat actors before they invest their time.
- Predictive analytics offer a competitive edge: Platforms like AppAware enable enterprises to anticipate attacks based on real-world intelligence.
- Security doesn’t have to slow innovation: With solutions like Digital.ai’s app-hardening tools, enterprises can protect apps at scale without disrupting developer workflows.
As generative AI continues to evolve, so too will the tactics used by hackers, and defenders must stay one step ahead. Digital.ai’s platform offers enterprise-grade solutions designed for this exact purpose: protecting applications at scale while enabling teams to innovate confidently.
Protect Apps & Neutralize Threats
Explore
What's New In The World of Digital.ai
When AI Accelerates Everything, Security Has to Get Smarter
Software delivery has entered a new phase. Since 2022, AI-driven…
The Invisible Wall: Why Secured Apps Break Test Automation
Modern mobile apps are more protected than ever. And that’s…
Evolving Application Security Documentation, One Step at a Time
In 2024, the documentation team at Digital.ai launched a new…