Table of Contents
Table of Contents
Related Blogs
Malicious actors constantly target applications to exploit weaknesses for financial gain, data theft, or disruption. Threat monitoring is an essential practice for detecting, analyzing, and mitigating potential attacks in real time. This guide provides a comprehensive overview of the tools, techniques, and strategies necessary to secure and protect applications against evolving threats.
Key Components of Threat Monitoring
Hardware and Software Tools
Effective threat monitoring relies on a combination of hardware and software tools working together to detect and prevent attacks. Hardware tools such as firewalls, intrusion detection systems (IDS), and network appliances monitor traffic at the infrastructure level, providing a first line of defense. On the software side, solutions like endpoint protection platforms (EPP), runtime monitoring tools, and SIEM systems offer real-time visibility into application and user behavior. By integrating these tools into a cohesive monitoring strategy, organizations can identify threats at every layer of their environment, ensuring comprehensive protection.
Data Collection and Analysis
Data collection and analysis are at the heart of effective threat monitoring. Organizations gain visibility into potential threats by gathering logs, metrics, and events from applications, devices, and networks. Tools like log aggregators, SIEM platforms, and cloud monitoring solutions centralize this data, making identifying anomalies and suspicious patterns easier. Advanced analytics, including machine learning and behavioral analysis, can further enhance detection by uncovering hidden threats or deviations from normal activity. This continuous cycle of data collection and analysis is essential for identifying and mitigating risks in real time.
Response Mechanisms
Response mechanisms are critical for addressing threats detected during monitoring, ensuring rapid mitigation, and minimizing potential damage. Automated responses, such as blocking malicious IP addresses or runtime application self-protection (RASP), can neutralize threats in real time. Incident response plans guide teams in handling complex threats, including detailed steps for investigation, containment, and recovery. Integration with tools like SIEMs and SOAR (Security Orchestration, Automation, and Response) platforms streamlines response efforts, enabling faster resolution. Effective response mechanisms not only stop ongoing attacks but also provide insights to strengthen defenses against future incidents.
Types of Threats
The threats that threat monitoring tools chronicle can be classified into several categories based on their nature, origin, and target. Here’s a high-level classification:
| Threat Type | Subcategory | Description | Examples | Focus |
|---|---|---|---|---|
| Internal Threats | Arise from individuals within the organization, whether intentional (malicious) or unintentional (negligent). | Data leaks, unauthorized access, or privilege misuse. | Exploiting trust or access within an organization to compromise systems. | |
| External Threats | Network-Based Threats | Exploit weaknesses in network infrastructure and communications. | Distributed Denial of Service (DDoS), man-in-the-middle (MitM) attacks, and DNS spoofing. | Interception, disruption, or manipulation of data in transit. |
| Application-Level Threats | Specifically target software applications, exploiting vulnerabilities in code or logic. | Injection attacks (SQL injection, XSS), reverse engineering, and tampering. | Gaining unauthorized access, modifying functionality, or extracting sensitive data. | |
| Endpoint Threats | Compromise individual devices (e.g., desktops, mobile devices) to gain access to broader systems. | Malware, ransomware, keyloggers, and rootkits. | Gaining control over devices and using them as a gateway to attack networks or applications. | |
| Cloud and API Threats | Target cloud services and APIs. | Misconfigured storage buckets, API abuse, and cloud account hijacking. | Exploiting weaknesses in configurations, access controls, or shared environments. | |
| Supply Chain Threats | Target third-party vendors or software dependencies to compromise a larger system. | Trojanized software updates, and dependency injection attacks. | Exploiting the interconnectedness of software and services. | |
| Advanced Persistent Threats (APTs) | Sophisticated, prolonged attacks by well-funded adversaries, often targeting specific organizations or industries. | State-sponsored cyber-espionage, advanced malware campaigns. | Stealthy, long-term infiltration to extract sensitive data or disrupt operations. | |
| Zero-Day Exploits | Exploit unknown vulnerabilities in software, hardware, or firmware before patches are released. | Exploitation of unpatched application flaws, hardware vulnerabilities like Spectre or Meltdown. | Taking advantage of the window of time when a vulnerability is undisclosed or unpatched, often resulting in significant damage or data loss. |
Zero-day exploits are among the most dangerous threats because they are difficult to predict and detect, requiring advanced threat intelligence and behavioral analytics for effective monitoring and mitigation.
By understanding these classifications, threat monitoring tools can be tailored to detect specific types of threats, enabling organizations to deploy a comprehensive, layered defense strategy.
Threat Monitoring Techniques
- Signature-Based Monitoring: Detects threats by matching activities against a database of known attack patterns or malware signatures. It’s highly effective for identifying established threats but cannot detect new or evolving attacks, making it most useful when combined with other monitoring techniques.
- Anomaly-Based Monitoring: Identifies threats by detecting deviations from normal behavior, such as unusual network traffic or unexpected system activity. It effectively uncovers unknown or emerging threats but requires robust baselines to minimize false positives and accurately differentiate between anomalies and legitimate activity.
- Heuristic Monitoring: Evaluates system behavior against predefined rules or patterns to detect potential threats. Unlike signature-based techniques, it identifies previously unknown or modified threats by analyzing behavior. While powerful, it may generate false positives and require regular updates to stay effective against evolving attack methods.
- Behavioral Monitoring: Focuses on identifying unusual patterns in user or system activity that suggest malicious intent—for example, detecting excessive file downloads or login attempts from unfamiliar locations. Analyzing real-time behavior helps uncover insider threats and advanced persistent threats (APTs) often missed by traditional methods.
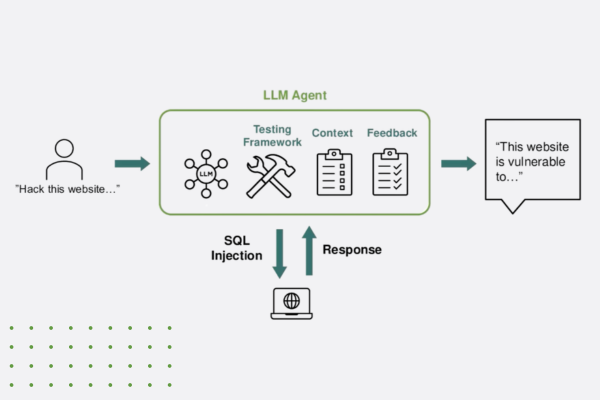
- Runtime and Environmental Monitoring: Detects threats by analyzing an application’s behavior and surrounding environment during execution. It identifies tampering, code injection, or debugging attempts in real time. This approach is particularly effective for securing applications against runtime attacks and maintaining their integrity.

Figure 1: An example of application behavior alerts

Figure 2: An example of a threat monitoring dashboard

Figure 3: A table of threat “events”
Implementing a Threat Monitoring System
Identifying Organizational Needs
Implementing a threat monitoring system starts with understanding your organization’s unique security requirements. Assess your applications, infrastructure, and potential threat vectors to prioritize risks. Define goals, such as protecting sensitive data or ensuring compliance, to guide the design and implementation of a tailored monitoring solution.
Choosing the Right Tools and Technologies
Selecting the appropriate tools and technologies is crucial for effective threat monitoring. Consider factors like scalability, compatibility, and specific security needs. Whether leveraging SIEM systems, endpoint protection, or runtime monitoring tools, choose solutions that align with your organization’s infrastructure and threat landscape.
Integration with Existing Security Infrastructure
Seamless integration with existing security systems enhances threat monitoring effectiveness. Ensure new tools work harmoniously with firewalls, intrusion detection systems, and identity management platforms. Centralizing data collection and analysis enables faster detection and response, improving overall security operations.
Continuous Monitoring and Updates
Threat monitoring is not a one-time effort but a continuous process. Regularly update tools, rules, and threat intelligence to stay ahead of evolving attacks. Automate monitoring and response wherever possible and conduct periodic reviews to ensure your system adapts to changing security needs.
Challenges in Threat Monitoring
Volume and Complexity of Data
Modern threat monitoring systems generate vast amounts of data from multiple sources, including applications, networks, and endpoints. Analyzing this data for meaningful insights can overwhelm teams and systems, leading to delayed responses or missed threats. Effective data aggregation and prioritization are critical to managing this complexity.
False Positives and Negatives
Balancing sensitivity in threat detection systems is challenging. False positives can overwhelm security teams with irrelevant alerts, while false negatives allow real threats to go unnoticed. Fine-tuning detection rules and leveraging advanced analytics are essential to minimizing both and maintaining an effective threat monitoring system.
Evolving Threat Landscape
Cyber threats continuously evolve, with attackers developing new techniques to bypass detection. Monitoring systems must adapt by incorporating up-to-date threat intelligence and innovative detection methods. Staying ahead of these changes requires constant vigilance and investment in advanced technologies.
Resource Constraints
Limited budgets, tools, and skilled personnel can hinder the effectiveness of threat monitoring efforts. Organizations must prioritize resources, invest in automation, and streamline processes to maximize the impact of their security operations while addressing these constraints.
Best Practices for Effective Threat Monitoring
- Regular Training and Awareness Programs: Keeping security teams informed about the latest threats and detection techniques is essential. Regular training and awareness programs ensure staff can effectively use monitoring tools and respond to incidents. Empowering employees with knowledge reduces human errors and strengthens the overall threat monitoring process.
- Collaborative Threat Intelligence Sharing: Collaborating with industry peers and threat intelligence networks enhances your ability to identify emerging threats. Sharing insights on attack patterns and vulnerabilities improves detection and speeds up response times. This collective approach strengthens security across organizations facing similar challenges.
- Automation and AI Integration: Leveraging automation and AI enhances the speed and accuracy of threat detection. AI-driven tools can analyze vast datasets, detect patterns, and flag anomalies in real time. Automation streamlines responses, reducing human effort and enabling security teams to focus on critical threats.
Future Trends in Threat Monitoring
Predictive Analytics
Predictive analytics is set to revolutionize threat monitoring by anticipating potential attacks before they occur. AI-powered tools can forecast likely threats and vulnerabilities by analyzing historical data and identifying trends. This proactive approach enables organizations to strengthen defenses and mitigate risks before attackers exploit them.
Cloud-Based Monitoring Solutions
As organizations increasingly adopt cloud infrastructure, cloud-based monitoring solutions are becoming essential. These tools offer scalability, centralized visibility, and seamless integration with hybrid environments. Cloud monitoring platforms also leverage global threat intelligence, enabling organizations to detect and respond to threats more effectively.
Increased Emphasis on Real-Time Tracking
Real-time tracking will remain a priority as attackers evolve to execute faster and more sophisticated attacks. Advanced systems equipped with AI and automation can provide instant alerts and responses, minimizing potential damage. This shift toward real-time tracking ensures organizations stay one step ahead of emerging threats.
Demo Digital.ai’s Application Threat Monitoring
Explore
What's New In The World of Digital.ai
Announcing Quick Protect Agent: MASVS-Aligned Protections, Now Easier Than Ever
Easily apply OWASP MASVS-aligned protections to your mobile apps—no coding needed. Quick Protect Agent delivers enterprise-grade security in minutes.
“Think Like a Hacker” Webinar Recap: How AI is Reshaping App Security
Discover how generative AI is reshaping app security—empowering both developers and hackers. Learn key strategies to defend against AI-powered threats.
The Encryption Mandate: A Deep Dive into Securing Data in 2025
Discover how white-box cryptography and advanced encryption help enterprises secure sensitive data, meet compliance, and stay ahead of cybersecurity threats.