Catalyst Blog
Featured Post
SEARCH & FILTER
More From The Blog
Search for
Category
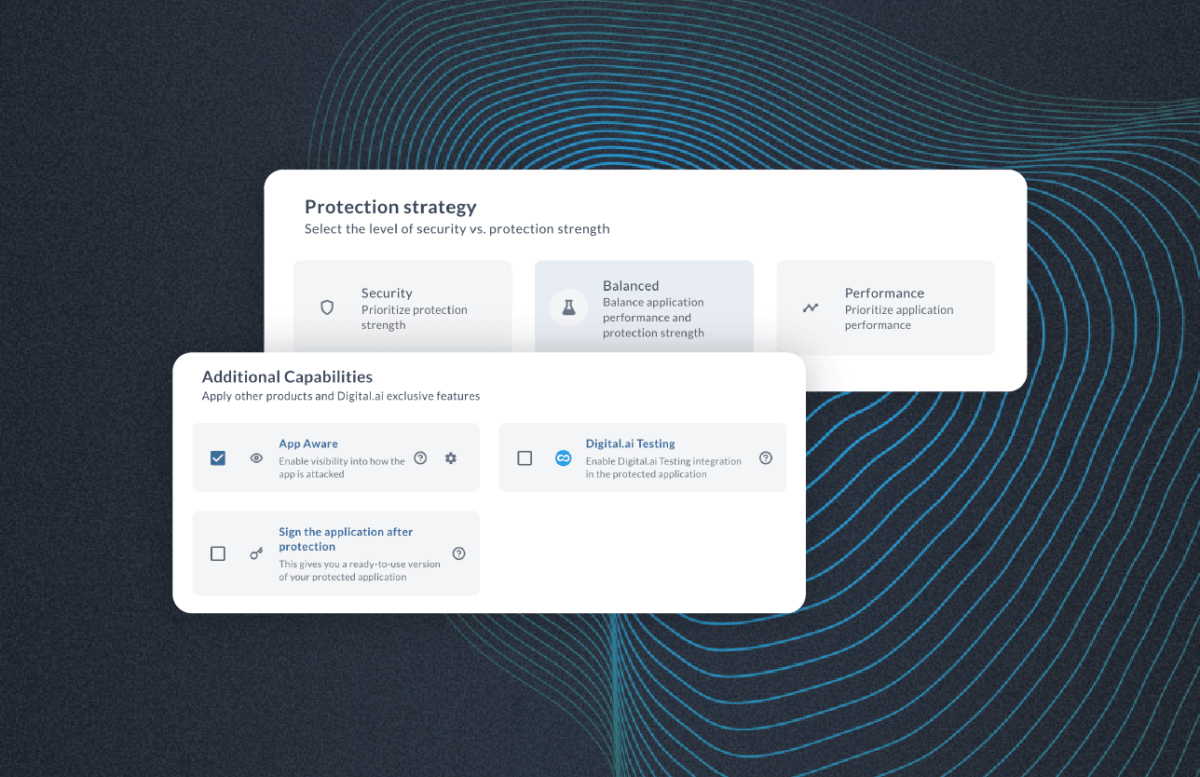
Protect Every Mobile App You Ship — No Matter How You Built It
Here’s the simple truth about the modern mobile landscape: There…
The Devs Guide to Synthetic Data Generation and Self-Cleaning Test Environments
In 2026, the biggest hurdle in shipping software isn’t how…
From Defense Labs to Mobile Apps: How Application Protection Grew Up
2001 was a turning point for application security, though few…
Escalations Aren’t Noise: They’re Your Most Honest Quality Signal
Most companies insist they care about product quality. Yet many…
Automating QA for Automotive Applications
Whether you’re building a music app, an EV charging service,…
When AI Accelerates Everything, Security Has to Get Smarter
Software delivery has entered a new phase. Since 2022, AI-driven…
The Invisible Wall: Why Secured Apps Break Test Automation
Modern mobile apps are more protected than ever. And that’s…