Are you ready to scale your enterprise?
Explore
What's New In The World of Digital.ai
When AI Accelerates Everything, Security Has to Get Smarter
Software delivery has entered a new phase. Since 2022, AI-driven…
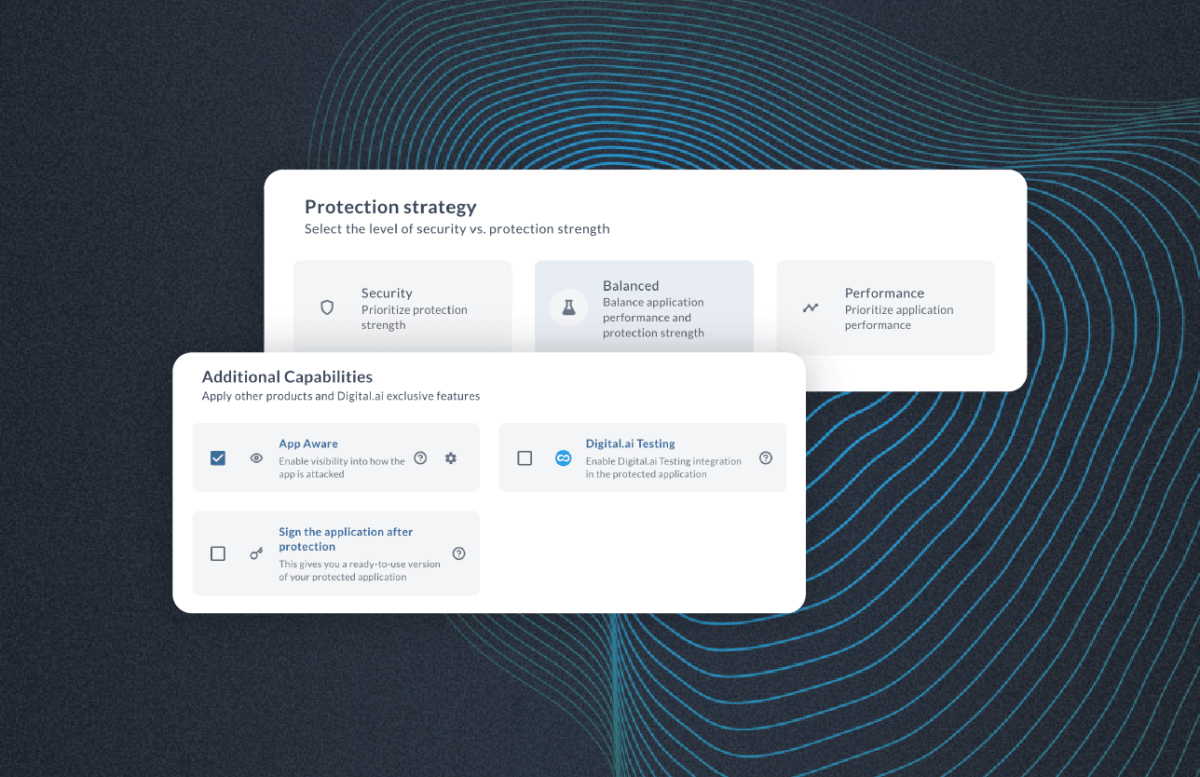
The Invisible Wall: Why Secured Apps Break Test Automation
Modern mobile apps are more protected than ever. And that’s…
Evolving Application Security Documentation, One Step at a Time
In 2024, the documentation team at Digital.ai launched a new…