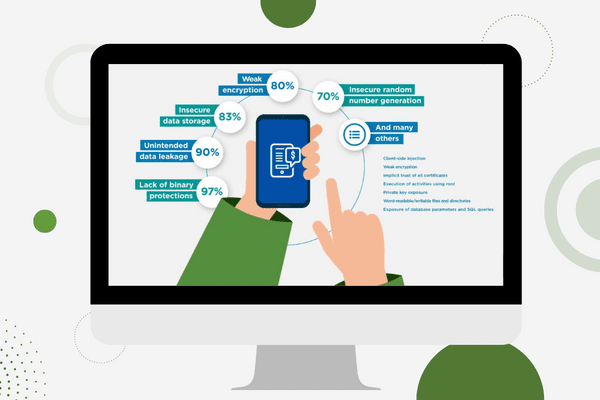
What is Application Hardening?
Application hardening is a means of protecting applications from reverse engineering by applying obfuscation and anti-tamper techniques to the application post build and pre-production.
Application hardening, also known as “Application Shielding” and “In-app Protection” is a means of protecting applications from reverse engineering by applying obfuscation and anti-tamper techniques to the application post build and pre-production. Application Hardening can also encompass application monitoring and RASP (Runtime application Self Protection).
Applications that have been “hardened” or “shielded” typically have the following security measures added to them:
- Binary level code obfuscation to prevent attackers from seeing a functional view of an application.
- Application integrity checks ensure the application code has not been altered.
- Anti-tampering mechanisms to detect whether the app is running on a rooted or jailbroken device.
- Ability to vary how protections are applied in each build to prevent attackers from building up a cumulative understanding of how apps are being protected.
- Runtime Application Self Protection or “RASP” that allow actions to take place if an app is being attacked or a device is determined to be compromised.
- Utilize white-box cryptographic protection to encrypt critical keys and data.