Table of Contents
Related Blogs
Overview of Security in Web Applications
Web applications are integral to delivering rich, interactive experiences to users. However, the convenience they provide also brings significant security challenges. Web applications operate within a complex ecosystem where both client-side and server-side components interact, often across multiple networks and devices. Ensuring the security of these applications requires a comprehensive approach that addresses potential threats at every layer of this architecture. From safeguarding the client-side (where users interact with the app and threat actors have full access to application code) to protecting server-side processes and data storage, a robust security strategy must be in place to mitigate the risks posed by a constantly evolving threat landscape.
Importance of Understanding Client-Side vs Server-Side Security
Understanding the fundamental differences between client-side and server-side security is crucial for effectively securing a web application. Client-side security focuses on the code and functionality in the user’s browser, making it inherently more vulnerable to attacks since threat actors can easily access, analyze, and modify the code. Techniques like obfuscation are essential to prevent reverse engineering and tampering. On the other hand, server-side security deals with the back-end infrastructure where sensitive data processing and storage occur. While server-side components are typically more protected within controlled environments, they can still be vulnerable to attacks such as SQL injection, cross-site scripting (XSS), and distributed denial of service (DDoS). Developers must secure both sides of the application to provide a seamless and secure user experience. Failing to address security on either end exposes the entire system to potential exploitation.
Client-Side Security
Definition and Importance
Client-side security is often overlooked but is critical in safeguarding web applications. Since the code executed on the user’s device is fully accessible and readable, threat actors can use exposed back-end server access instructions to launch various attacks. Protecting the client-side requires understanding the range of threats and implementing measures like code obfuscation to make exploitation more difficult. Below, we will explore several common threats to client-side security, each posing unique risks that can undermine the integrity of your application if left unaddressed.
Common Threats
Reverse Engineering
Reverse engineering is a method used by threat actors to decompile and analyze the code of a web application to uncover its inner workings, business logic, and potential vulnerabilities. Since client-side code is fully accessible to users, it becomes an easy target for reverse engineering attempts. Attackers use specialized tools to deobfuscate, debug, and study the code, potentially revealing sensitive information like API keys, encryption algorithms, or authentication mechanisms. This process allows them to bypass security controls, tamper with the application, or even create counterfeit versions. To mitigate reverse engineering risks, developers must employ techniques like code obfuscation and encryption to make the code difficult to understand, deterring threat actors from easily exploiting it.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a common client-side threat where attackers inject malicious scripts into web pages viewed by other users. These scripts can be executed in the victim’s browser, allowing attackers to steal session cookies, hijack user accounts, redirect users to malicious websites, or even deface the web application. Attackers exploit weaknesses in user input handling through XSS attacks, particularly when data is not properly sanitized or validated. They can be especially dangerous because they execute within the context of a trusted web application, making detection difficult. Developers must ensure that all user inputs are properly escaped, validate inputs on both the client and server sides, and implement Content Security Policies (CSP) to restrict the execution of untrusted scripts to protect against XSS.
Magecart
Magecart is a collective term for a group of cybercriminal groups–and an attack technique–that specializes in injecting malicious scripts into web applications, primarily targeting e-commerce platforms. Magecart attackers can intercept sensitive data such as credit card information and personal details during checkout processes by exploiting exposed client-side code. Attackers often launch these attacks through compromised third-party services or JavaScript libraries that web applications load. Once they inject the malicious code, it can silently siphon data, evading detection for long periods. Protecting against Magecart requires implementing strong client-side security measures, such as code obfuscation, ensuring the integrity of third-party scripts, and employing Content Security Policies (CSPs) to prevent unauthorized script execution.
Cross-Site Request Forgery (CSRF)
Cross-site request forgery (CSRF) is an attack that tricks a user’s browser into making unauthorized requests to a web application in which they are authenticated. By leveraging the user’s credentials, attackers can perform actions such as changing account settings, transferring funds, or even executing malicious commands on behalf of the victim—all without the user’s knowledge. CSRF attacks exploit the trust a web application places in a user’s browser, often through social engineering techniques like phishing or by embedding malicious links in third-party websites.
Malicious Script Injection
Malicious script injection is a dangerous attack where threat actors inject unauthorized or harmful scripts into a web application’s client-side code. This can happen through compromised third-party libraries, browser plugins, or vulnerabilities in user input handling. Once injected, these scripts can execute within the user’s browser, allowing attackers to steal sensitive information, manipulate page content, or even launch further attacks on other users. Malicious script injections often go undetected by users since the code appears to be part of the legitimate application.
Security Measures
Input Validation and Sanitization
Input validation and sanitization are fundamental security measures that help protect web applications from a wide range of client-side attacks, including cross-site scripting (XSS) and SQL injection. Input validation ensures that data entered by users adheres to expected formats, rejecting any input that deviates from predefined criteria. This prevents malicious actors from injecting harmful code into input fields. Meanwhile, sanitization cleanses the input data by removing or escaping potentially dangerous characters. This process ensures that even if attackers insert malicious scripts, the system won’t execute them. These two processes together form the first line of defense against client-side threats, significantly reducing the attack surface by controlling and cleansing all incoming data before it reaches the application’s core logic.
Content Security Policy (CSP)
Content Security Policy (CSP) is a powerful security feature that helps protect web applications from client-side attacks like cross-site scripting (XSS) and malicious script injection by controlling what resources can be loaded and executed in the browser. CSP allows developers to specify which scripts, styles, and other content can be sourced and executed, reducing the risk of malicious code being injected or executed within the application. By setting strict CSP rules, such as restricting external scripts and limiting inline script execution, web applications can block unauthorized scripts from running, even if attackers manage to inject them into the code. This added layer of defense helps mitigate threats that target client-side vulnerabilities, ensuring that only trusted sources can interact with the application.
Secure Cookies
Secure cookies are essential for safeguarding sensitive data, particularly in web applications where user authentication and session management rely heavily on cookies. By marking cookies with the `Secure` attribute, developers ensure that cookies are only transmitted over encrypted HTTPS connections, preventing them from being exposed to man-in-the-middle attacks. Additionally, setting the `HttpOnly` attribute restricts access to cookies from client-side scripts, protecting them from being stolen in cross-site scripting (XSS) attacks. The `SameSite` attribute adds another layer of security by preventing cookies from being sent along with cross-site requests, mitigating the risk of cross-site request forgery (CSRF). By using secure cookies, web applications can better protect user sessions and reduce the chances of unauthorized access to sensitive information.
HTTPS and TLS
HTTPS (Hypertext Transfer Protocol Secure), powered by Transport Layer Security (TLS), is critical for ensuring secure communication between the client and server in web applications. HTTPS encrypts data in transit, preventing threat actors from intercepting or tampering with sensitive information like login credentials, session tokens, or personal data. TLS, the encryption protocol behind HTTPS, ensures the integrity and confidentiality of this data by using strong cryptographic methods to protect against eavesdropping and man-in-the-middle attacks. Additionally, HTTPS helps authenticate the server, assuring users that they are interacting with the legitimate web application. Enforcing HTTPS across the entire application and maintaining updated TLS versions and configurations are essential steps to protect client-server communication and enhance overall security.
Obfuscating Client-Side Web Code
Obfuscating client-side web code is a crucial security measure designed to protect sensitive application logic from being easily understood and exploited by threat actors. Since client-side code is fully accessible to anyone using the application, obfuscation scrambles the code, making it difficult for attackers to read or reverse-engineer. By transforming variable names, control structures, and logic flows into unreadable formats, obfuscation creates a significant barrier for those attempting to deconstruct the application. While obfuscation does not prevent access to the code, it dramatically raises the effort required to decipher and manipulate it, providing a layer of security that helps protect against reverse engineering, tampering, and other malicious activities. Implementing obfuscation is essential for safeguarding the client-side of web applications.
Tools for Client-Side Security
A range of tools are available to help developers strengthen client-side security and protect against common threats. Digital.ai Web Application Security is a robust solution that provides features like code obfuscation, anti-tamper protection, and real-time threat monitoring, specifically designed to safeguard client-side code from reverse engineering and malicious attacks. Snyk is another popular tool that helps developers identify and fix security vulnerabilities in open-source libraries used in web applications, providing real-time alerts for known risks. Burp Suite is widely used for penetration testing, allowing security teams to assess and identify client-side vulnerabilities like XSS and CSRF. Additionally, OWASP ZAP (Zed Attack Proxy) is an open-source tool that scans web applications for various vulnerabilities, including XSS and injection flaws. Together, these tools offer a comprehensive toolkit for developers to protect client-side code, detect vulnerabilities, and mitigate potential risks.
Server-Side Security
Definition and Importance
Server-side security refers to the protective measures implemented on the back-end of a web application, where critical processes, data storage, and user authentication occur. Developers fully expose client-side code to users, while they keep server-side components hidden and execute them in a controlled environment. However, this does not make them immune to attacks. Securing the server-side is essential because it handles sensitive information like user data, business logic, and communications with databases and APIs. Failure to properly secure these components can lead to severe breaches, including unauthorized data access, database manipulation, or full server compromise. Ensuring robust server-side security is vital to maintaining the integrity, confidentiality, and availability of the application, as it forms the backbone of secure operations.
Common Threats
SQL Injection
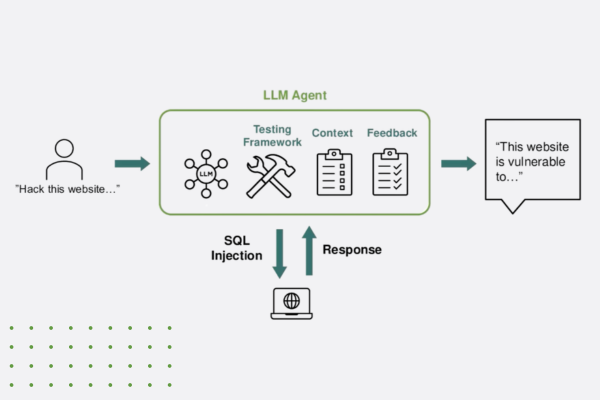
SQL injection is one of the most dangerous server-side threats, where attackers exploit vulnerabilities in an application’s input fields to execute malicious SQL queries on the back-end database. By injecting specially crafted code into input fields that are not correctly sanitized, attackers can manipulate the database, allowing them to gain unauthorized access to sensitive data, modify or delete records, or even take control of the entire database system. SQL injection can compromise a web application’s integrity and confidentiality, exposing user data and business-critical information. To defend against SQL injection, developers must ensure all user inputs are properly sanitized and parameterized queries are used, preventing attackers from executing arbitrary SQL code within the application.
Distributed Denial of Service (DDoS)
A Distributed Denial of Service (DDoS) attack aims to overwhelm a web server by flooding it with a massive volume of requests, rendering the application unavailable to legitimate users. In a DDoS attack, threat actors leverage a network of compromised devices (often called a botnet) to send traffic to the target server simultaneously, exhausting resources such as bandwidth, memory, or processing power. This can result in significant downtime, lost revenue, and damage to an organization’s reputation. While DDoS attacks do not compromise sensitive data, their ability to disrupt service makes them a serious threat to the availability of server-side applications. To mitigate the impact of DDoS attacks, organizations can use solutions such as rate-limiting, traffic filtering, and content delivery networks (CDNs) that can distribute traffic loads and absorb large-scale attacks.
Server Misconfiguration
Server misconfiguration is a prevalent server-side security threat that occurs when servers are improperly set up, leaving critical systems vulnerable to attack. Misconfigurations can include issues like exposed default settings, unused services that remain active, insufficient access controls, or unpatched software. These oversights provide attackers with easy entry points to exploit, allowing them to gain unauthorized access, modify settings, or even take control of the server. Misconfigured servers can also inadvertently expose sensitive data to the public, increasing the risk of data breaches. Regularly auditing server settings, applying patches, disabling unnecessary services, and enforcing strong access controls are key practices to prevent misconfigurations and ensure that servers are secured against potential exploits.
Security Measures
Authentication and Authorization
Authentication and authorization are critical security measures that ensure only legitimate users can access and perform specific actions within a web application. Authentication verifies the identity of users, typically through methods like passwords, multi-factor authentication (MFA), or biometric verification, ensuring that users are who they claim to be. Once authenticated, authorization determines what actions or resources the authenticated user can access based on predefined roles and permissions. Effective authentication and authorization processes protect sensitive data and functionality by preventing unauthorized users from gaining access or manipulating server-side components. Implementing secure authentication protocols, such as OAuth or OpenID Connect, and enforcing strict role-based access control (RBAC) are essential to safeguard server-side resources.
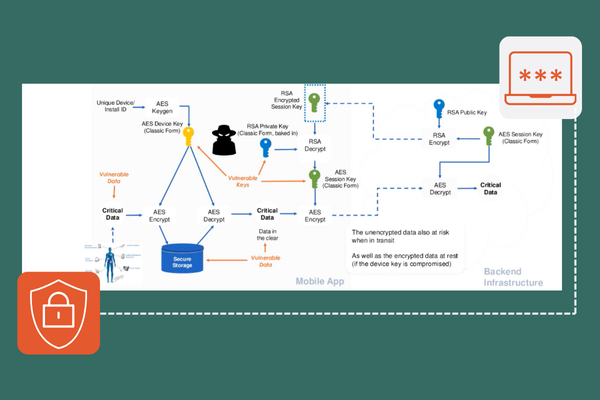
Encryption of Data at Rest and in Transit
Encryption is a fundamental security measure for protecting sensitive data while it’s stored (data at rest) and when it’s being transmitted between clients and servers (data in transit). Data at rest—files, databases, and backups—can be encrypted using strong algorithms like AES to ensure that even if unauthorized parties can access the storage, they cannot read or manipulate the information. Data in transit, including user inputs and server responses, should be encrypted using Transport Layer Security (TLS) to prevent interception or tampering during communication. These encryption practices protect against unauthorized access, ensuring that sensitive data remains confidential and integral, even in the face of breaches or eavesdropping attempts.
Web Application Firewalls (WAF)
A Web Application Firewall (WAF) is a security solution designed to protect web applications by monitoring and filtering incoming traffic. By analyzing HTTP requests and responses in real-time, WAFs can detect and block common attack patterns, such as SQL injection, cross-site scripting (XSS), and distributed denial of service (DDoS) attacks. By acting as a shield between the user and the server, WAFs help mitigate the risk of malicious traffic reaching the server, ensuring that only legitimate requests are processed. WAFs are an essential layer of defense, providing continuous protection against both known and emerging threats.
Tools for Server-Side Security: Enhancing Backend Protection
Several tools are available to help bolster server-side security and protect against common threats. Imperva and Akamai provide a Web Application Firewall (WAF) that shields applications from threats like SQL injection and DDoS attacks by filtering malicious traffic. Prolexic protects against DDoS attacks, automatically scaling to absorb large volumes of traffic. Tripwire is widely used for server-side vulnerability management, helping organizations identify and address misconfigurations, patching gaps, and potential security risks. Leveraging these tools ensures that server-side components remain protected against a wide range of threats.
Best Practices for Comprehensive Web Security
Combining Client-Side and Server-Side Security
Ensuring comprehensive web security requires a balanced focus on client- and server-side protection. While client-side security focuses on safeguarding code that runs in users’ browsers, server-side security protects the back-end processes and data. Effective web security strategies must integrate both sides to mitigate a wide range of threats. For instance, obfuscating client-side code prevents reverse engineering, while server-side authentication and encryption protect sensitive data. A unified approach ensures that vulnerabilities on either end do not compromise the entire application, creating a seamless and secure user environment. By combining these layers of security, organizations can better protect themselves from modern attacks that target both sides of the application.
Continuous Monitoring and Incident Response
Continuous monitoring and incident response are essential to a comprehensive web security strategy. Cyber threats evolve rapidly, making it crucial to have real-time visibility into potential vulnerabilities and attacks. Implementing continuous monitoring tools helps detect unusual activity, such as unauthorized access attempts or performance anomalies, which could signal an ongoing attack. In conjunction with monitoring, a well-defined incident response plan ensures swift action when security breaches occur, minimizing damage and reducing recovery time. Automating alerts, integrating security tools with a Security Information and Event Management (SIEM) system, and conducting regular drills ensure your team is prepared to quickly identify, contain, and mitigate any threats.

Use Obfuscation to Strengthen DevSecOps
Explore
What's New In The World of Digital.ai
Announcing Quick Protect Agent: MASVS-Aligned Protections, Now Easier Than Ever
Easily apply OWASP MASVS-aligned protections to your mobile apps—no coding needed. Quick Protect Agent delivers enterprise-grade security in minutes.
“Think Like a Hacker” Webinar Recap: How AI is Reshaping App Security
Discover how generative AI is reshaping app security—empowering both developers and hackers. Learn key strategies to defend against AI-powered threats.
The Encryption Mandate: A Deep Dive into Securing Data in 2025
Discover how white-box cryptography and advanced encryption help enterprises secure sensitive data, meet compliance, and stay ahead of cybersecurity threats.