Application Security
Harden applications against reverse engineering attempts, monitor threats to applications, and build runtime application self protection (RASP) into the apps you make and give to your customers.
Protect, Monitor, React and Test
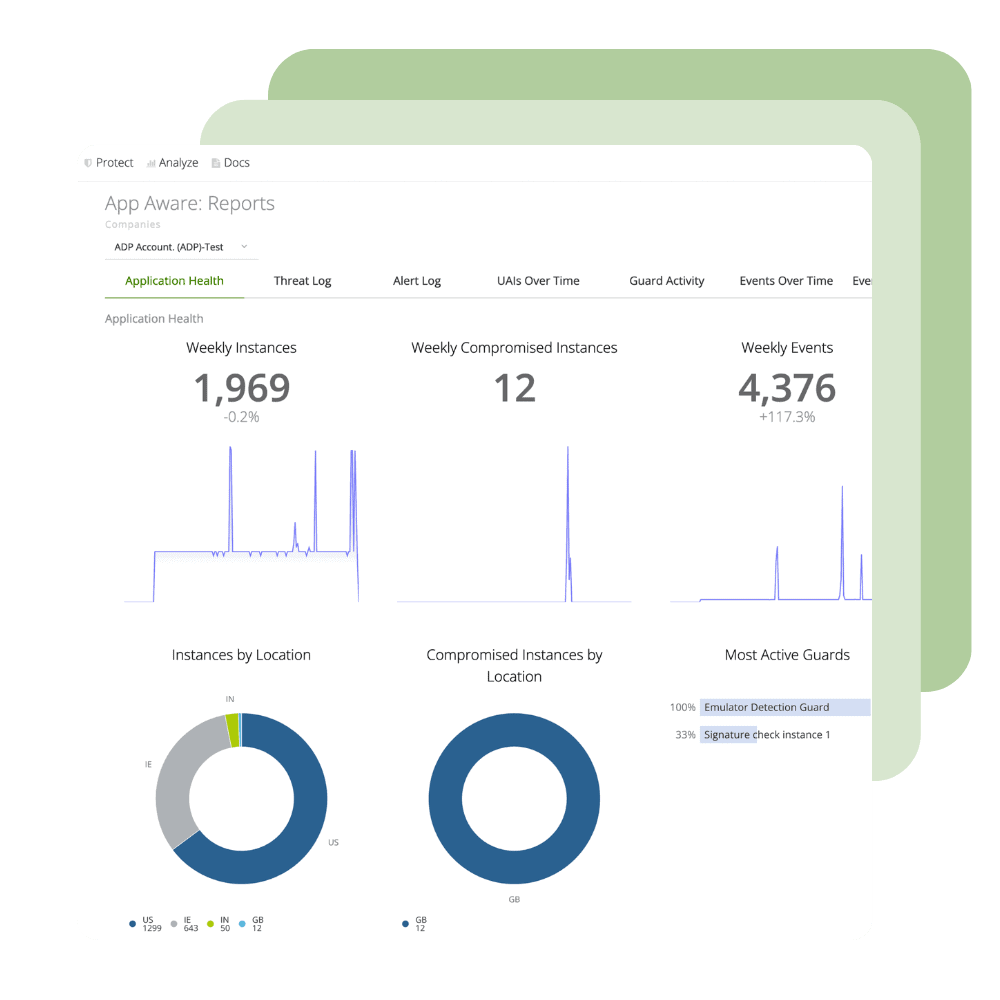
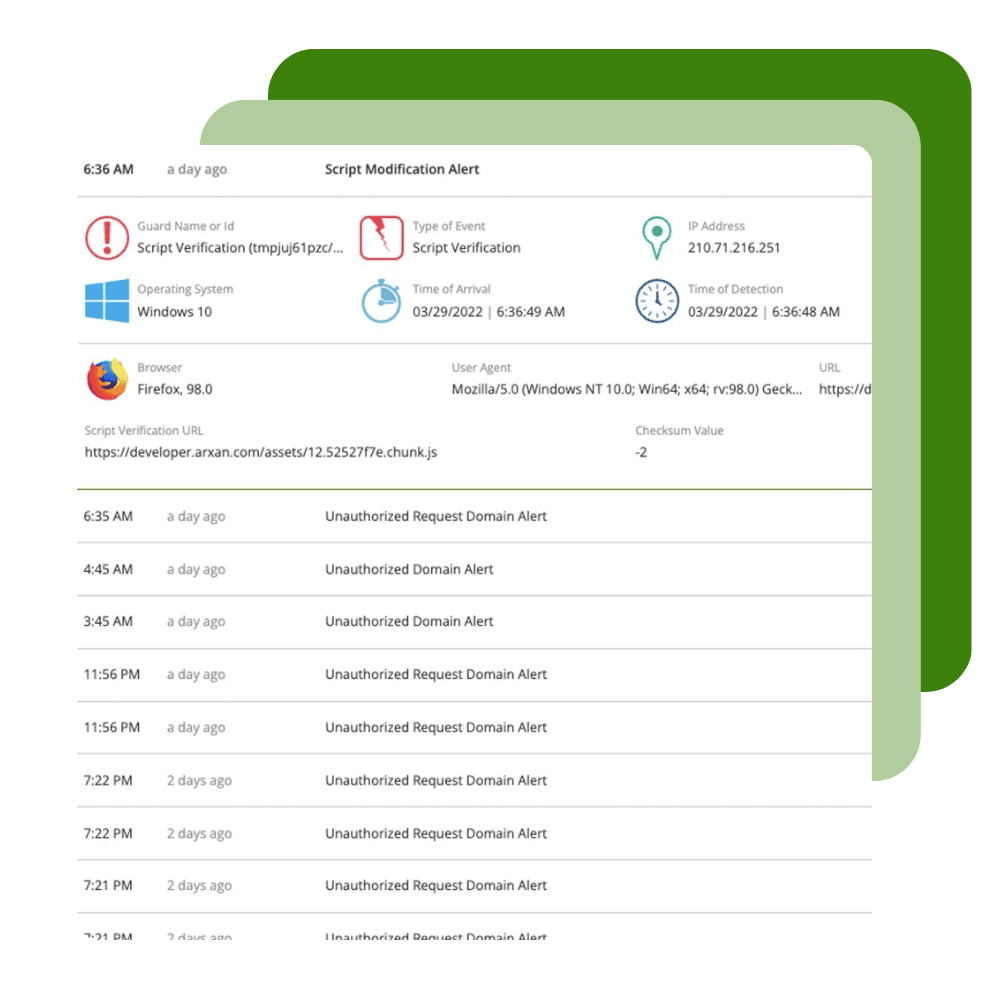
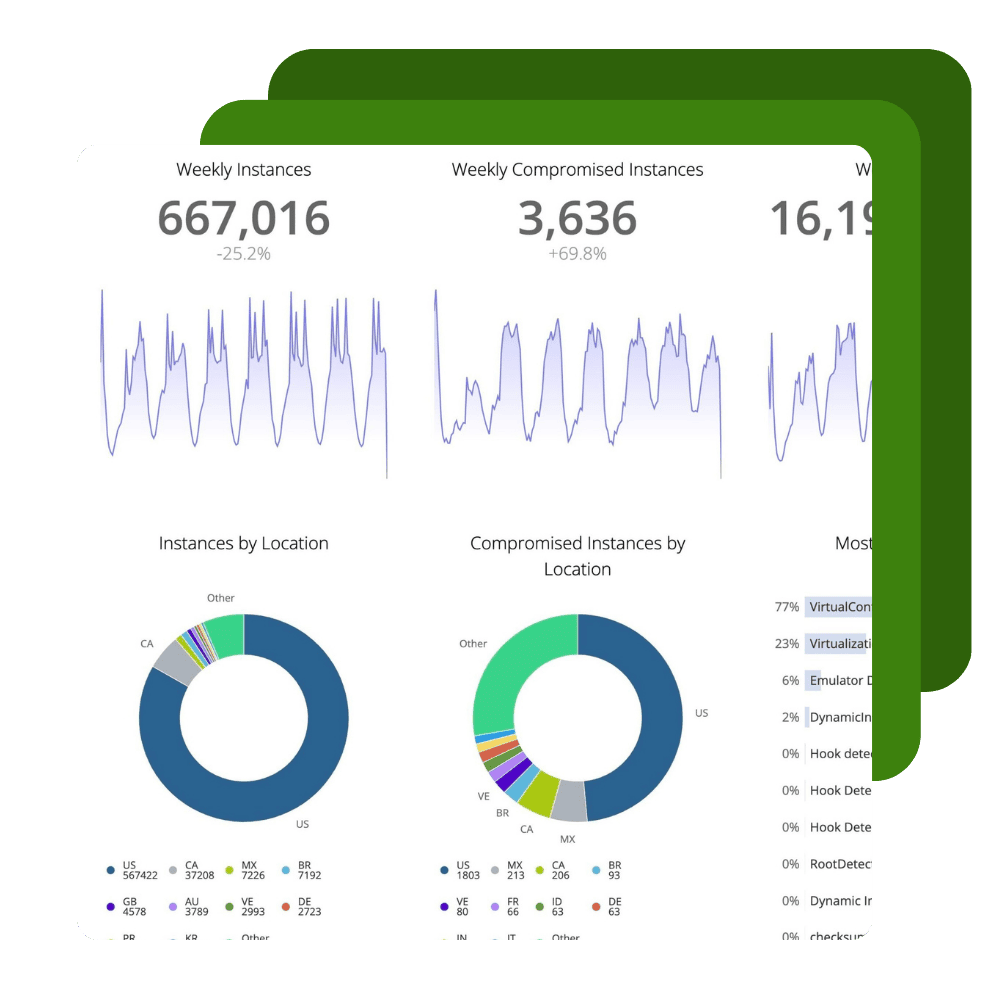
Ignite your DevSecOps practice by inserting security into your apps at the build phase. Harden your application against reverse engineering, build the ability to monitor threats to your apps in production directly into your SDLC, and create apps that have the ability to automatically react to threats to apps through Runtime Application Self-Protection (RASP). Get up and running in minutes with our Quick Protect Agent. Perform automated performance, functionality, and accessibility testing from Digital.ai Continuous Testing -- without triggering anti-tamper protections.
Build Secure Software to Prevent Reverse Engineering
Protecting the following types of Mobile/Web/Desktop apps
We can protect applications built using the following languages/frameworks
Cordova
Flutter
Ionic
C/C++
Swift/Objective-C
React Native
Unity
.NET (Maui)
Xamarin
Java/Kotlin
JavaScript
Native Script
Rust
Capabilities
Rising Attacks on Client Apps—Are Your Defenses Keeping Up?


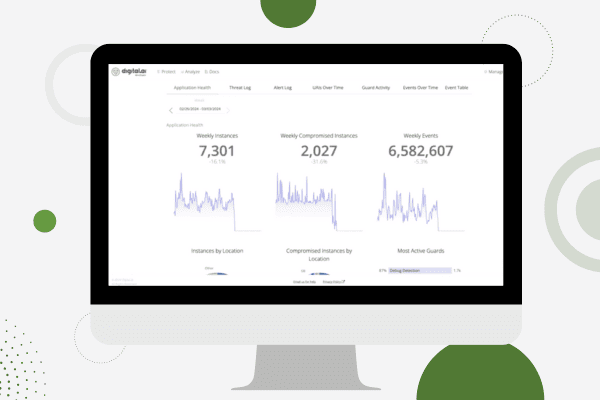
See Digital.ai Application Security in Action
We have helped thousands of enterprises protect, monitor and react to attacks on the apps they make and give to their customers. Contact us to learn more.