Table of Contents
Related Blogs
In our digital-first world, where mobile apps dominate customer interactions and sensitive data flows across decentralized networks, cybersecurity is no longer a back-office concern—it’s a boardroom priority. This was the central theme of Digital.ai’s recent webinar, “The Encryption Mandate: Secure Data or Risk Noncompliance,” featuring Lou Crocker, Principal Consultant.
Crocker’s session was a call to action for enterprises to rethink how they secure their most valuable asset: data. Let’s revisit the key takeaways from the webinar and connect them to the broader cybersecurity conversations shaping 2025.
The Perfect Storm of Cybersecurity Challenges
Crocker opened the discussion with an unflinching look at the current threat landscape, saying, “Every application and device in the world today are running on the same network. Therefore, perimeter security is no longer sufficient or, in many cases, even effective. We’ve become an API centric world.”
Businesses inadvertently expand their attack surfaces as they embrace mobile-first strategies and cloud-native architectures. Mobile apps alone are expected to generate nearly $1 trillion in revenue this year, but each app also represents a potential threat risk.
The rise of generative AI (GenAI) has further complicated matters. While AI accelerates innovation, it also empowers cybercriminals to automate attacks, bypass traditional defenses, and exploit applications at scale. Ransomware, social engineering, and data exfiltration remain top threats, but what’s truly alarming is the shift in hacker priorities: They’re no longer content with stealing individual credentials—they want entire datasets.
This aligns with broader industry observations. According to the World Economic Forum, ransomware remains the most significant cyber risk globally, while AI-powered malware is becoming increasingly sophisticated. For enterprises, this means that securing endpoints—whether mobile apps or IoT devices—is now mission-critical.
Compliance: The Business Case for Encryption
In 2025, compliance isn’t just about avoiding fines; it’s about protecting your brand and earning customer trust. Crocker highlighted three key regulatory frameworks that demand robust encryption measures:
- GDPR: Enforces strict rules on protecting personally identifiable information (PII) and mandates encryption as a best practice for ensuring data confidentiality.
- HIPAA: Requires encryption for all protected health information (PHI) at rest and in transit to safeguard patient data.
- PCI DSS: Sets stringent standards for securing financial transactions, emphasizing encryption as a core requirement.
But compliance is only half the battle. Crocker stressed that traditional encryption methods often fall short in today’s threat landscape. Hackers can exploit how cryptographic keys are stored or transmitted, rendering even compliant systems susceptible to breaches.
This echoes a growing sentiment among cybersecurity leaders: Compliance frameworks provide a baseline, but true security requires going above and beyond regulatory requirements.
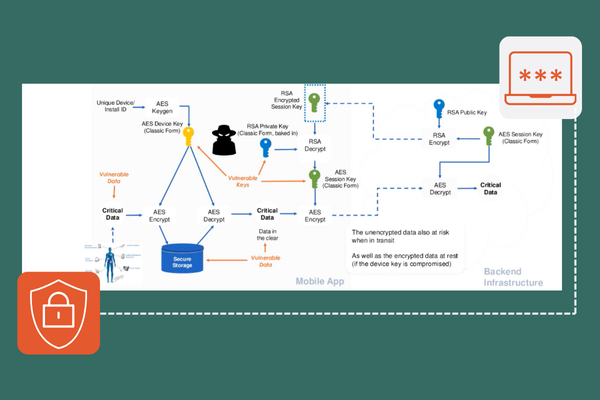
White-Box Cryptography: A Paradigm Shift
Let’s delve into white-box cryptography—a technology designed to secure cryptographic keys even in untrusted environments. Unlike traditional cryptography, where keys can be exposed during runtime or stored insecurely, white-box cryptography keeps keys hidden at all times.
Here’s how it works:
Cryptographic keys are transformed into “white-box” keys through a one-way mathematical operation. These keys are embedded within applications in such a way that they cannot be extracted or used outside their intended library. Even if an attacker gains access to the application’s runtime environment, they cannot use or reverse engineer the white-box keys.
Digital.ai’s white-box solution is FIPS 140-3 certified—meeting military-grade security standards while remaining practical for commercial use. Crocker illustrated this with a practical example: imagine a banking app that encrypts sensitive customer data before transmitting it to a server. With white-box cryptography, even if an attacker intercepts the communication or accesses the app’s runtime environment, they cannot decrypt the data without the matching library—a level of protection traditional methods simply cannot offer.
Connecting the Dots: Cybersecurity Trends and White-Box Cryptography
The insights shared during the webinar align closely with broader cybersecurity trends:
- AI as Both Threat and Opportunity: While AI-powered tools enable faster app development and anomaly detection, they also fuel more sophisticated cyberattacks. White-box cryptography provides a critical defense against these evolving threats by securing data at its core.
- Zero Trust Architectures: As enterprises adopt zero trust principles—where every access request is continuously verified—white-box cryptography complements this approach by ensuring that even compromised endpoints cannot expose sensitive data.
- Future-Proofing Against Quantum Computing: With quantum computing on the horizon, organizations are exploring quantum-resistant algorithms to protect their data long-term. White-box cryptography offers a scalable solution that addresses both current and future challenges.
Why This Matters Now
Crocker didn’t mince words when summarizing the stakes: “Security is a journey, not a destination.” In an era where cyber risks evolve daily, enterprises must prioritize encryption as part of a holistic security strategy. White-box cryptography isn’t just a technical solution—it’s a business enabler that allows organizations to innovate confidently without compromising security.
For enterprises handling sensitive data—whether PII, PHI, or financial information—the time to act is now. As Crocker aptly put it: “You can close your browser and say ‘This won’t happen to me’— or you can enjoy the peace of mind provided by a FIPS 140-3 certified data security posture and book a session with us.”
Final Thoughts
The webinar wasn’t just an educational session but a rallying cry for enterprises to embrace advanced encryption technologies like white-box cryptography. By doing so, organizations can not only meet compliance requirements but also gain a competitive edge in today’s digital economy.
At Digital.ai, we understand that security isn’t just about technology—it’s about trust. Our FIPS 140-3-certified solutions are designed to meet the complexity and scale of modern enterprise environments while providing peace of mind in an increasingly uncertain world.
Ready to elevate your security posture? Let’s start the conversation today and ensure your organization is prepared for whatever comes next.
Elevate Your Security Posture & Ensure Compliance
Explore
What's New In The World of Digital.ai
When AI Accelerates Everything, Security Has to Get Smarter
Software delivery has entered a new phase. Since 2022, AI-driven…
The Invisible Wall: Why Secured Apps Break Test Automation
Modern mobile apps are more protected than ever. And that’s…
Evolving Application Security Documentation, One Step at a Time
In 2024, the documentation team at Digital.ai launched a new…